Until December 2017, Google Groups containing hundreds of University communications and associated documents with restricted, confidential, or otherwise sensitive information had misconfigured permission settings such that anyone who could access the Boston College G Suite—known formally as Google Apps—could view them, a Heights investigation found.
The Heights notified the University on Dec. 18 of this vulnerability. BC Information Technology Services (ITS) immediately secured the vulnerability that day, but it was not until the week of March 19 that Google instituted a platform-wide modification. The Heights withheld publication of this article until a wider fix was implemented, as publishing this story before that change could have made other institutions that use G Suite more vulnerable in the event that they also had misconfigured privacy settings.
Nora Field, BC’s deputy general counsel, said in an email that no other access to confidential information occurred outside of the Heights investigation. The Heights was using Google Groups for other purposes before discovering this vulnerability and notifying the University.
The Heights never retained any information contained in any of these groups.
All of these records and communications were visible as a result of the email list feature of Google Groups, a web app available to anyone with access to BC’s G Suite.
“Since transitioning to Google [Apps] in 2013-2014, all current BC faculty and staff are able to access Google Groups,” David Escalante, director of computer policy and security, said in an email. All currently enrolled students are also able to access G Suite services including Groups, Gmail, Drive, and others.
Google Groups allows any BC user to create mailing lists that deliver emails to specific recipients, but also adds all the messages and attachments to the Google Group associated with the mailing list. Due to misconfigured privacy settings, some of these groups and the communications sent on such mailing lists—some of which contained confidential, restricted, or otherwise sensitive information—were accessible and searchable to those in the BC community.
Google’s fix now allows all IT administrators who manage G Suite to modify the default privacy settings for all newly created Google Group mailing lists. Previously, there was not a way to modify the default access level from “public” across an organization. Now, the setting can be changed by administrators such that “private” is the default, meaning only those specified will be able to access it. Domain administrators could previously only set privacy levels on an individual, group-by-group basis, and the creator of the mailing list had to specify “private” in place of the default setting when setting up their list.
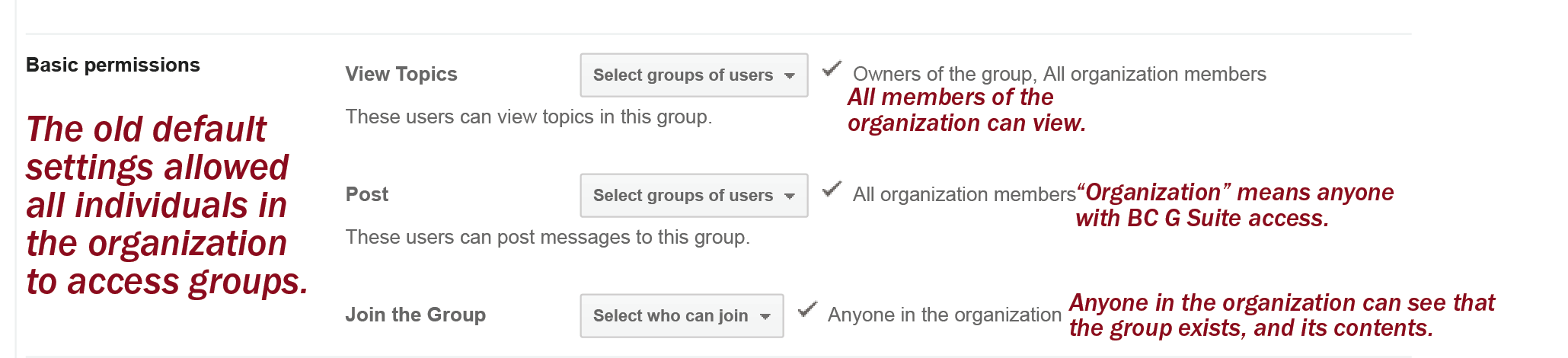
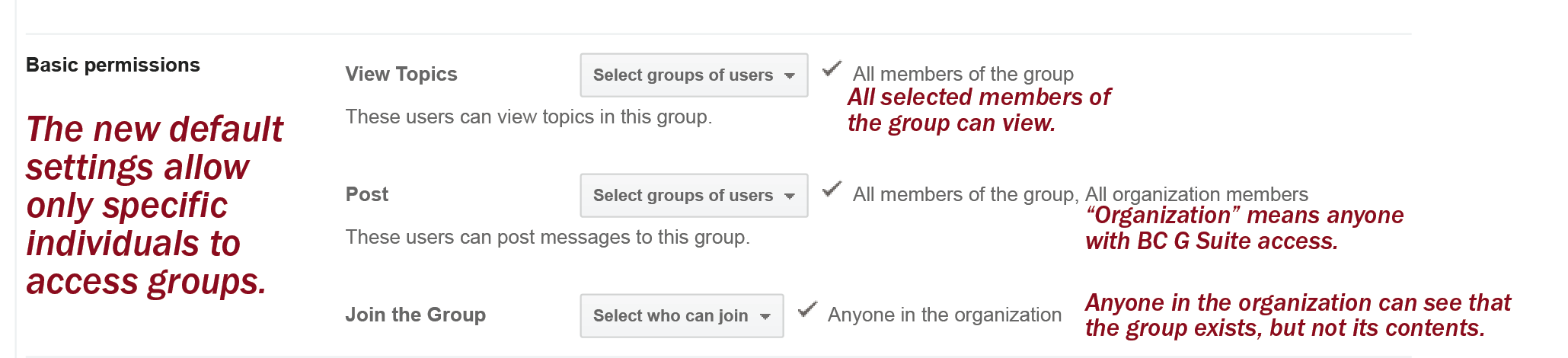
Prior to this change, group creators still had the ability to select a private option when creating a group, even though it was not the default. Some BC administrative groups, for example, had privacy settings that restricted access to only specific users. The Office of the Executive Vice President, Office of Residential Life, and Office of Undergraduate Admission, for example, all had settings such that neither the content nor the list of group members was accessible except to those with proper credentials.
Some of the communications and records accessible were what appeared to be thousands of internal emails retained in Google Groups for the Boston College Police Department. Some of these correspondences contained confidential, restricted, or otherwise sensitive information, including police logs and incident reports.
A query on Google Groups of a person’s name or event in which BCPD was involved, therefore, could have potentially returned correspondences and associated documents that BCPD would not consider “public.”
“BCPD used Google Groups without realizing that access to their message archives was not properly restricted through Google. That issue has since been rectified,” University Spokesman Jack Dunn said in an email.
BCPD policy requires an incident report to be filed for “each significant incident (i.e., those that involve a criminal act or serious breach of University rules), or if it appears advisable for any reason to retain a permanent and readily accessible record.” According to the “FAQ” section on BCPD’s website, these records are not permitted to be publicly released. This differs from the public BCPD blotter, which describes generally—and anonymously—only the nature, time, date, general location and (if applicable) the disposition of the complaint. According to the policy that outlines the functions and responsibilities of BCPD, only the blotter is considered a public record.
Among the documents accessible was BCPD’s Executive Summary. This is a daily, confidential list with the previous day’s police activity. These reports contain a detailed summary—including people’s names—regarding these incidents. When The Heights notified the University of the vulnerability, Executive Summary reports from April 2017 through Dec. 18, 2017 were accessible.
One accessible BCPD group that contained confidential, restricted, or otherwise sensitive information had privacy settings mistakenly permitting “anyone from the bc.edu organization” to “view content,” “join,” “post,” and “view the list of members” in the group, rather than being restricted to those within BCPD. The Heights identified similar access settings across other BCPD internal groups in which confidential, restricted, or otherwise sensitive information existed.
Another accessible document accessible in a BCPD group included the first and last name of a member of the BC community, their Massachusetts State Driver’s License number, and other identifying information. Another included the first and last name of a different member of the BC community, their social security number, and other information. The combination of a person’s first and last name, social security number, Massachusetts state identification or driver’s license number, or various financial information constitute “Personal Identifiers” under Massachusetts 201 CMR 17.
According to the Office of Consumer Affairs and Business Regulation for the Commonwealth of Massachusetts, BC filed a report on Feb. 5, 2018 that an unspecified number of Massachusetts residents experienced a data “breach” (as defined by the Commonwealth) with regard to their social security number. It is unknown whether this unspecified number of individuals has been contacted by the University about the breach.
Also accessible—through non-BCPD groups—were confidential documents related to University Advancement, including names of some individual and corporate donors, and various monetary amounts they had donated to the University. Documents related to a consulting firm used by BC for fundraising work and internal documents with strategies on donor relations were also accessible.
The Heights made no attempt to access any groups that were not publicly accessible, nor to access any systems based on information identified within these communications.
“The students involved have assured the University that they did not retain or disclose any confidential information, and the University has concluded that no further breach notifications are required at this time,” Nora Field said in her email.
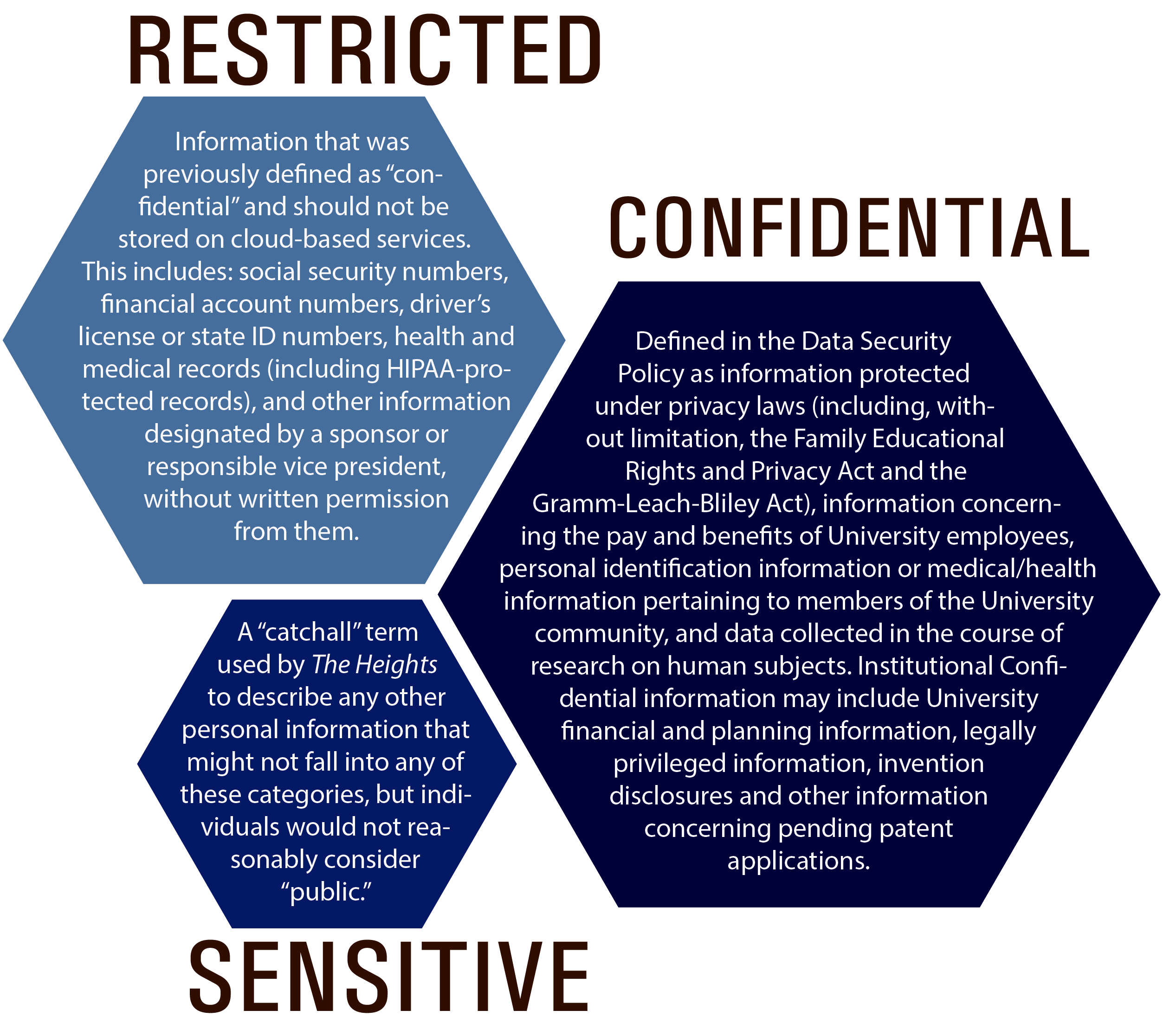
The University’s Data Security Policy, last revised in 2010, defines three levels of classification for what is colloquially considered “sensitive” information. Officially, these are “Public,” “Internal Use Only,” and “Confidential.”
According to the document, examples of confidential data include: “information protected under privacy laws (including, without limitation, the Family Educational Rights and Privacy Act and the Gramm-Leach-Bliley Act), information concerning the pay and benefits of University employees, personal identification information or medical/health information pertaining to members of the University community, and data collected in the course of research on human subjects. Institutional Confidential information may include University financial and planning information, legally privileged information, invention disclosures and other information concerning pending patent applications.”
After adopting G Suite in 2015, however, BC indicated that a “fourth category of data … even more sensitive than ‘confidential’” known as “restricted” exists, and that such information, formerly classified as confidential—such as social security numbers, financial account numbers, driver’s license or state ID numbers, health and medical records, including HIPAA-protected records, and other information designated by a sponsor or responsible vice president—could not be stored on off-campus servers, including any of Google’s services, without written permission of the responsible vice president or provost.
In recent years, other universities have experienced incidents where various kinds of protected information has been improperly secured. In February 2017, an email list service maintained by the Harvard Computer Society was discovered to mistakenly have settings such that over 1.4 million emails were publicly accessible. Some of these communications included information about students’ grades, financial aid information, and other confidential material. Harvard Dean of Students Katherine G. O’Dair responded in an emailed statement that “her office was working to ensure student privacy.”
In November 2017, The Stanford Daily reported that approximately 200 students and employees might have had their privacy compromised due to incorrect permission settings on a University-managed server. Some of these documents included information for reporting statistics under the Clery Act, though only one document was reported to include a student’s name. Stanford University released a statement on Dec. 1 regarding the issue.
In 2005, the BC Chronicle reported that because of a security breach of a third-party-owned computer that contained about 100,000 alumni social security numbers, the University “decided to send out a precautionary advisory to those alumni whose names were on the database with Federal Trade Commission guidelines they could follow to help ensure their privacy.” In that incident, there was no indication that any personal information was accessible to members of the BC community.
*Editor’s Note: The Heights respects your privacy. Our reporting on this topic has spanned over three months, and during this time the authors have made every attempt possible to ensure the privacy of any individuals mentioned in the then-publicly accessible communications. Names were neither recorded nor shared. None of these communications were retained.
Steven Everett is the Creative Director for The Heights. He can be reached at [email protected].
Connor Murphy is the Editor-in-Chief for The Heights. He can be reached at [email protected].